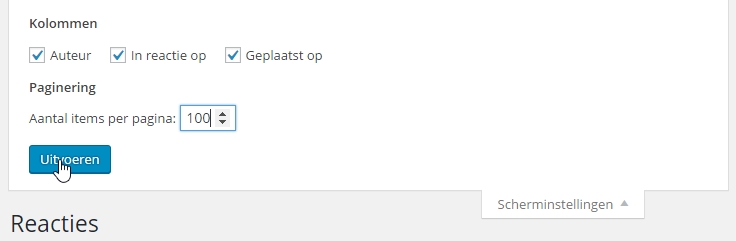
WordPress Security is like a Pyramid

The Base is WordPress
At the top of the pyramid, it all begins with the programmer/designer who sets up your WordPress website.
Securing Just One Part is Useless!
Focusing on one aspect, such as having a good programmer/designer, secure passwords, or the latest updates, won’t be enough. As you can see from the pyramid, it’s just one part of the whole.
A Truly Secure WordPress Website
To achieve a genuinely secure WordPress website, you need to secure all aspects.
We will help you, step by step, to make each part of the pyramid secure so that your WordPress website is truly protected!
- The Programmer/Designer
- The Theme
- The Plugins
- The Hosting
- The User
- WordPress Itself
The Programmer/Designer
A good WordPress website developer will use no more than 8-10 plugins. Each additional plugin is an opportunity for hackers, as not all plugin developers are experts in security.
This is where knowledge comes into play; the programmer/designer needs to be aware of the risks associated with each additional plugin and should consider coding certain features instead of relying on plugins.
However, bear in mind that a programmer/designer may take longer to create functions without using plugins, so the budget may need to increase! You can’t expect a programmer to build a fully functional website for a small amount (150-300) and also ensure top-notch security. (Also, not every programmer who charges a lot of money is necessarily good!!)
The Theme
Whether it’s premium or free, it doesn’t matter.
Really?
Premium themes are more frequently targeted by hackers because they prefer to hack sites that involve money. Premium plugins are commonly used, and hackers know that.
In short, being premium is not a guarantee. Do some research to see if the theme is listed in this database.
The Plugins
As shown in the pyramid, plugins play a significant role in the website’s security, with more than 36.3% of the website’s security depending on them.
Plugins are “third-party made,” which means they are developed by individuals in their basement or by teams launching a plugin.
Do you know who made your plugin? And do they have expertise in security?
There are 44,273 plugins available for free download on WordPress.org.
This is a fantastic offering! Plugins such as:
These are excellent plugins that can transform WordPress into an online shop or marketing machine!
However, once they gain popularity, hackers download the plugins and search for vulnerabilities. Once found, they create a script that scans websites for the presence of the targeted plugin and then executes a script to fill your website with ads, advertising the hacker’s products. Often, these products are related to Viagra, as it apparently sells well??
The Hosting
Hosting is where your website resides. This is known as a “data center.”
Sounds cool, and it is. High-tech computers are running to serve your website.
Well, high-tech… they are actually expensive stripped-down computers!
Powerful processors and ample storage ensure that websites are served quickly when a visitor requests them.
What is the host’s responsibility?
The host must ensure that the server software is up to date. The websites are displayed via a computer running Linux or Windows, and these should not get infected/hacked. This rarely happens, which is why this accounts for only 9.09% in the pyramid.
What does a good host do?
A good host wants to keep their high-tech computers fast, meaning they ensure that websites are being visited while hacker scripts are not active. Sometimes, a hosting company might ask you to keep all WordPress plugins up to date.
Or they might even take your WordPress website offline!
If your website is busy sending spam or launching attacks on other servers/computers of the host, they may take your website offline to stop this disruptive behavior.
The User

What You, as a User, Can Do
- Keep your plugins, theme, and WordPress up to date
- Choose passwords that are not easy to guess
- Don’t leave unnecessary plugins or themes on the server
- Avoid clicking on links while logged in as the website’s administrator
WordPress Itself
The developers behind WordPress, who continue to offer it for free, are very active. They release new WordPress updates on a monthly, and sometimes even more frequent, basis to address new hacker tricks.
WordPress itself is a good and stable system! It was launched in May 2003 and has been in development for over 10 years.
Did You Know?
There is a Dutch security plugin that takes care of 80% of these aspects for you!
iThemes Security PRO NL
This plugin helps you set up
the server/hosting, enforces the use of strong passwords, keeps hackers out, secures directories, stops brute force attacks, secures your admin area, and provides an overview and control over your website!
—
Please note that some Dutch words/phrases (e.g., programmer, theme, plugins, hosting, user, WordPress) have been left untranslated for context and clarity.