If you’re new to Nulled plugins, they are “free” premium plugins that contain malware.
Nulled plugins are bought by criminals, loaded with malware and then offered for free.
The paradox
An antivirus plugin that should keep out hacks and hackers, who has been hacked?!
That’s like putting a security guard in your store from Thief & Co
A security guard who arrives on time every morning with an empty backpack, likes to work overtime and goes home with a full backpack.
False security!
The special thing is that there are enough people who illegally download premium plugins without paying properly and thus fall into the trap of the hackers.
Many do not realize that from the moment the plugin becomes active, the website sends spam or redirects visitors in the first session to a website where you can gamble or buy other strange items.
This is detrimental to your position in Google and to your turnover, since your visitors will not see your website in this way.
The experiment
We regularly deal with WordPress sites that have been hacked because the programmer did not properly buy the plugins, but simply downloaded them illegally.
We thought it would be interesting to see what we get when we download a Nulled plugin for WordPress security.
Experience
We deal with hacked websites a lot and know exactly what we are doing. We do NOT recommend downloading illegal or Nulled plugins or other software.
Measures
Of course we don’t want viruses and we don’t want any problems with the server.
For that reason, we download the Nulled plugin on a virtual computer and put the plugin on a closed server.
Finding a Nulled plugin
There is nothing easier than googling and downloading a Nulled plugin. You can’t think of it that crazy or they offer it. The latest releases and the most expensive plugins.
But.. don’t be fooled, no matter how reliable and professional the website looks: the plugins contain hacks!
It’s already hit the first download!
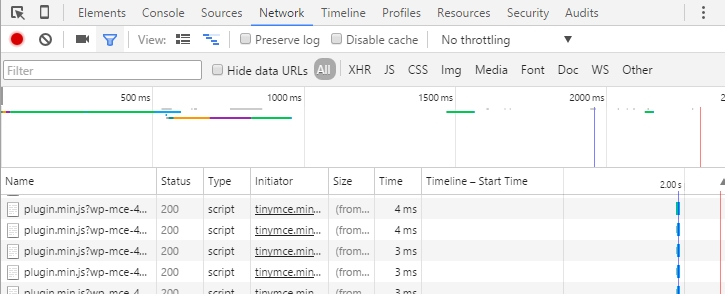
I scan the first Nulled plugin with VirusTotal. It hits immediately.
What you see on the screenshot below are the most rotten hacks: trojans & back doors.
Trojans work secretly in the background of your website without you realizing it.
The name is derived from the Trojan horse. (Those who don’t know that story, read the story here)

Trojans, backdoors, malware..
When you activate the plugin, you set access to your server & WordPress fully open. The hackers or an automated script will receive a signal which website has now been hacked (available).
They can do absolutely anything they want:
- Modify payment details in WooCommerce to their own illegal bank account
- Store and forward usernames and passwords
- Show advertising
- Edit texts
- Forward visitors
- And much more..
But there’s server security, right?
You would say that the security of the server, of the web host, knows this!
But that’s not true. The server does scan files, but the trick is that the plugins fragment the code and execute it in certain orders. Only the plugin itself knows that order, so the server cannot or will not execute it to find out that it contains unwanted code.
In addition to the fragmentation, the code is also written in an unreadable language that can only be executed by the hack itself.
The result can also not be judged as being desirable or not, since PHP has many server rights.
Only the most obvious and common hacks are detected and written as “suspected”.
Hacks do have a habit of exploiting server power and running everything at full speed. When the hoster finds out, they will disable your hosting package until you solve the problem.
The hoster cannot be held responsible for hacks in your website. You rent the web space, and if you don’t manage it properly or get hacked for whatever reason, it’s up to you to fix it.
Since that is complicated, do you need help or have your website repaired by professionals.
We dig deeper into the plugin
We have wandered off for a while, but we dig deeper into the plugin to see where those trojans and backdoors are.
Can we find them?
Looking for fragmented and encrypted code
Often server commands are encoded in Base64 and then executed with Eval. That’s the first thing we look for.
We see some lines of code appear (notepad++ Find in files).
But those lines of code look innocent.
Notable files
One technique we use when recovering a hacked website is to simply look for salient files.
Strange file names or php files that don’t belong in certain folders (like the css folder) often betray the malware/hacks.
We exclude a folder with css, a folder with images and a folder with txts.
But not so fast, the images are sometimes made executable!! (We don’t see any php extensions in the images and so continue)
Exclude files
We have excluded several files, and decide to scan the remaining files again.
It is striking that 2 of the 12 antivirus services do not realize that it concerns the previously tested malware after changing the name.
In short, they determine that a plugin is fake and only remember the name without scanning the content more often.
That is also one of the reasons why hacks/viruses can go on for so long, when minor changes in code or order of execution are made, they are unrecognizable by various antivirus services.
A few folders deep
Many hacks are a few folders deep, so they are less likely to be found. Somewhere between the “images” the “uploads/2015/etc” or “includes/colors/etc”
Not in this case, the trojans put them directly in the “core” files of the security plugin.
Found!
In the end we found the hacks, the code was neatly written.
It has been well thought out, several alternative methods have been used to open your website to the rest of the world (and especially to the hackers themselves).
Of course we do not show the code.
Conclusion
Nulled plugins still contain trojans. In these types of hacks, the code is neatly concealed with formatting so that it is indistinguishable from the regular code.
We will be doing more tests soon, such as:
- Is the antivirus plugin aware that it itself contains a hack/virus?
- Can other antivirus plugins find the hack in this plugin?
Stay informed of the latest messages via Linked-in, or via our news page!
Side note 1: hackers
And it should be clear that hackers and their criminal activities are not appreciated.
A hacker’s romance as you see it in movies is not how it goes in reality.
A hacker is someone who harms others for their own profit.
It frustrates the website owners, it frustrates the web hosting, and ultimately it costs money and time.
Side note 2: Illegal downloads
Well, if you choose to download something illegally yourself… you are actually just like the hackers.
You’re trying to take advantage of a plugin or theme without giving its creator their hard earned money.
We’ve all downloaded something from the internet, right?
But at least now you know what NOT to download illegally from the Internet.
Ps: we buy software that we work with neatly. Even if it’s just to avoid problems 😉
Safety above all!