All my WordPress websites have been hacked, now what?
What’s in this article
- several websites hacked at once, how is that possible?
- how do you know your websites have been hacked?
- how to prevent a hack?
Plugins or themes regularly leak and malware ends up in multiple WordPress websites at the same time.
Wwhat should you do if you are responsible for 5 or 10 websites? Or when you manage 80 to 100?
Multiple websites hacked at the same time, how is that possible?
When 1 plugin is used on multiple websites or when 1 fixed theme is used, there is a greater chance that several websites will be infected at once.
Hackbots perform searches for certain plugins with a leak and use the leak to fill the website with advertising, spam, malware, backdoors and more trouble.
1 hack – 1 solution?
You would think that you can find the hack in the same files or folders on every website. Or in 1 fixed place in the database.
Unfortunately, hack scripts use the technique of dropping malware in random places.
Randomly posting hacks are done by the hack scripts to prevent the server from intercepting
In short, you have to solve and remove 1 hack in different ways.
Help to find hacks in your websites
Malcare
Malcare is a service that allows you to check multiple websites for hacks.
You have to register them 1-by-1, but once registered, Malcare shows exactly which files contain the malware.
It is then up to you to determine whether you want to manually remove the hacks/malware, or whether the files need to be completely removed.
The sucuri malware scan
The malware scanner from Sucuri shows you what hacks you have. This will help you find and remove hacks.
Google webmaster tools
The security page of the Google webmaster tools tells you which pages contain malware, phishing or unwanted advertising. find is.
Is there a One Click Fix to make all hacked websites hack-free in 1x?
We all prefer to see a “one click fix”. Where the computer/software detects and removes or corrects the hacks.
Unfortunately, there is no one-click fix as the difference between a hacker’s code and desired code cannot be calculated by software.
The tools we described above make it a lot easier to find the hacks among the hundreds of files and the thousands of lines of code, but you will still have to remove or modify the hacks yourself.
How do you know your websites have been hacked?
If WordPress has been hacked you will not immediately see it, the hacks themselves are usually well hidden by a hacker and his script/virus.
Usually you can see the effect of the hack.
- Your website is being redirected to another website.
- Your website shows advertisements or links from another website in your website. (You can read why hackers do that here.)
- You can no longer access your administration panel.
- Your website has completely changed its style or even shows a page from the hacker.
- Your website is slow.
- The security of your computer reports Phishing, a Trojan or other attacks on the PC.
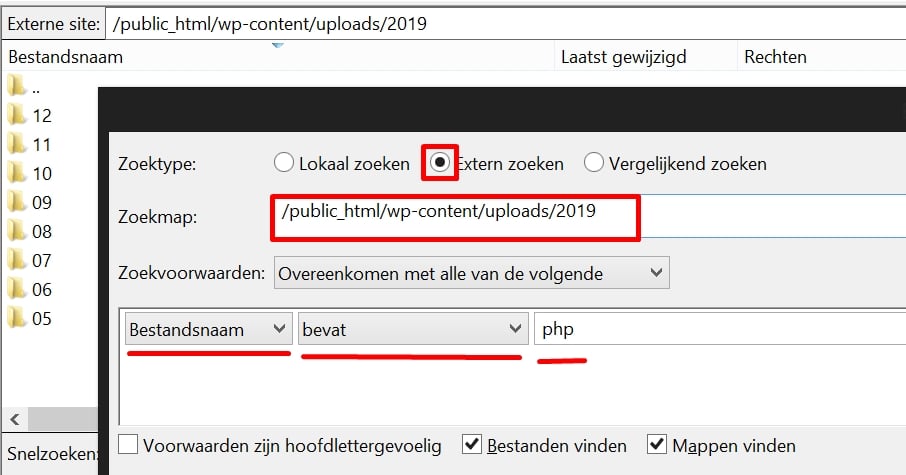
You can do a scan if you are not sure if your websites have been hacked:
Rescan.pro – Good at detecting malware, hacks.
Sucuri malware scanner – Shows you if the site contains malware and often shows what type of malware
IsItHacked – Sees iframes and other hacker tricks before previous scanners
Remove the hack, what are you looking for?
Hackers use various methods to hide malware from the server’s virus scanner and from you so you can’t get it out easily.
Think of it as a thief, who also prefers not to be seen and has various tricks and disguises for that.
Base64
This is code that is executed through specific requests on files. The virus scanner does not make those requests, so the code remains hidden.
Base64 is an ugly plain line of code, usually containing the base64 declaration and/or an eval.
Note that some plugins also use base64. With base64 you can convert entire images into code!
Neat code intertwined with current coding
In some situations, hackers write clean code with professional formatting so that you can hardly tell the difference between code that belongs in the website and that of the hacker.
Java scripts
They load external files by means of 1 small piece of code. Those files contain all the hacks. Because the code is loaded externally, it cannot be found in your website. Fortunately, the aforementioned Sucuri & rescan scanner that does handle javascripts.
Code in disguised files
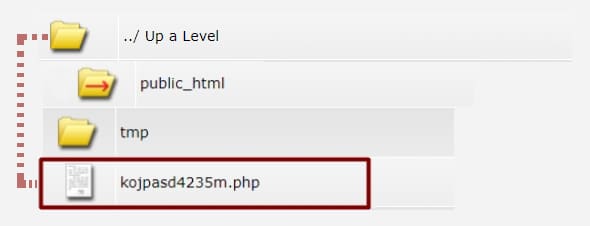
Code in “images”. A png file is an image type that the server will not execute as code. But with proper encryption, hackers can open the png and run it as a script. The server and other antivirus programs and especially people look over those “innocent” images in the uploads folders!
How to prevent all your WordPress sites from being hacked
- Install an antivirus plugin on every website
Every website needs protection against automated hacks, viruses and/or malware. - Make regular backups
Preferably make daily backups, at least once a week. Retains at least 4-8 weeks as it sometimes takes about 3 weeks before you find out that malware has entered your website through a hack. - Check the websites regularly
Check the security plugins logs for suspicious file changes, login attempts, etc - Keep plugins and themes up to date
The programmers of plugins regularly release updates that fix security vulnerabilities - Do not use more than 8-15 plugins per website
Every plugin is a security risk - Keep premium plugins and themes up to date as well
Make sure the licenses are valid, premium plugins may be better maintained by the programmers but they are also targeted by hackers.
Hackers download Nulled versions of the premium plugins and can test them for possible security risks for free - Put each website on a unique hosting package or user account
We regularly see multiple websites in 1 hosting package. The risk of this is that all sites are hacked if the ftp/database data leaks.
And what is most common is that the malware can be placed in all folders.
Prevent this with separate hosting packages or users under a VPS. This way you limit the write permissions and sites cannot exchange malware with each other.