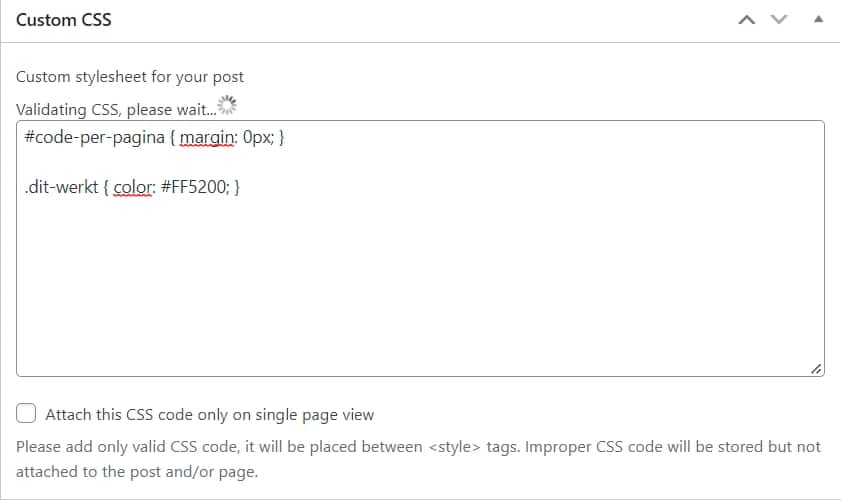
Hackers – actually automated hackbots/scripts, do everything they can to hide their malware well in the server between your WordPress core files, the uploads folders, or between the plugins. There is some strategy behind placing malware and there are specific folders where hackers usually hide their malware.
In which folders can you often find Malware in a hack?
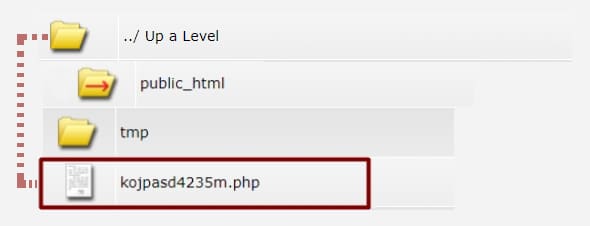
Look in the folder above the public_html
The folder where your website resides is usually called public_html, www, or httpdocs.
Above (or in front of) those folders you have other server folders, and with a bit of bad luck, a hacker or script got access to those folders above and hid the malware there….
Ps: Keep in mind that sometimes you can’t even access those upper folders with a standard ftp program and a standard ftp account.
Look in the uploads folders
Many plugins have write permissions and access to uploads folders that are freely writable.
Therefore, all it takes is a small modification to a leaky plugin to store unwanted files.
With an extensive directory structure spanning years and months, there are plenty of places to hide malware!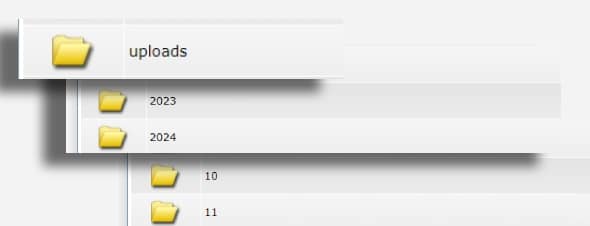
Look in the WordPress base folders
WordPress itself is also where hackers often put files, think of the wp-includes and the wp-admin folder.
Look in plugins & theme folders
Many websites have between 7 and 30+ plugins, enough space to place a few unsavory files!
Waarom de mappen boven de public_html & de uploads mappen de grootste voorkeur genieten bij hackers en hackbots? Dat is omdat de map boven de public_html + de uploads mappen niet ge-update worden waardoor de malware er langer kan blijven staan.
Sluw hè?
Naast de beste verstopplekken om malware neer te zetten worden er ook diverse verstop-strategieën gebruikt. Hackers en bots hebben strategieën om de malware zo lang mogelijk in je website te houden.
De strategie bij het plaatsen van malware plaatsen
Strategie 1: het script zet de malware in elke map!
Als een hack eenmaal in je server is binnengedrongen gaat zo’n hack in 20% van de gevallen over tot het verstoppen van malware in ELKE MAP. In de hoop dat je er 1 vergeet wanneer je de hack probeert te verwijderen. De kans dát je de malware vind, of dat de malware door de server ontdekt wordt is groter, maar ja.. zie maar eens GEEN enkele map over het hoofd te zien bij het verwijderen!
Strategie 2: het script zet de malware alleen 3 mappen diep
Voor een script is het gemakkelijk om alleen malware te plaatsen in mappen met 3 lagen bovenliggende mappen. De malware wordt op deze manier zo ver mogelijk UIT HET ZICHT geplaatst.
Strategie 3: het script zet de malware IN een bestaand bestand
Dit zijn de ergste! Dan is de malware IN een bestaand bestand geplaatst. Je zult dan heel specifiek naar een lijn code op zoek moeten.. een speld in een hooiberg als je niet weet hoe je moet zoeken!
Oké, je hebt nu een idee WAAR je malware kunt gaan zoeken. Nu vraag je jezelf natuurlijk af: hoe herken ik een virusbestand, malware bestand of hack tussen tientallen legitieme noodzakelijke bestanden?
Dat kun je in het volgende artikel lezen: ,,Zo herken je een virus bestand“.
Why the folders above the public_html & the uploads folders are most preferred by hackers and hackbots? It’s because the folder above the public_html + uploads folders don’t get updated which allows the malware to stay there longer.
Smart huh?
In addition to the best hiding places to put malware, various hiding strategies are also used. Hackers and bots have strategies to keep malware in your website for as long as possible.
The strategy when placing malware places
Strategy 1: The script puts the malware in every folder!
Once a hack has penetrated your server, in 20% of cases such a hack proceeds to hide malware in EVERY MAP. Hoping you will forget one when you try to remove the hack. The chance that you find the malware or that the malware is discovered by the server is higher, but hey… try NOT to overlook a single folder when deleting it!
Strategy 2: the script only puts the malware 3 folders deep
It is easy for a script to place malware only in folders with 3 layers of parent folders. This way, the malware is placed as far as possible OUT OF THE SIGHT.
Strategy 3: the script puts the malware IN an existing file
These are the worst! This is when the malware is placed IN an existing file. You will then have to look very specifically for a line of code…a needle in a haystack if you don’t know how to search!
Okay, you now have an idea WHERE to look for malware. Now of course you are asking yourself: how do I recognize a virus file, malware file or hack among dozens of legitimate necessary files?
You can read about that in the following article: ”How to recognize a virus file”.