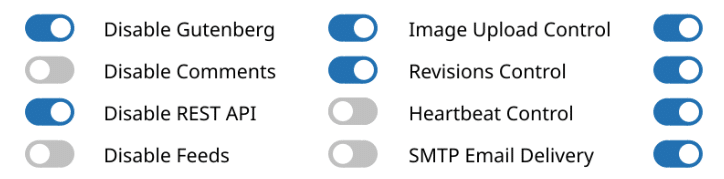
BitFire Security – In vuur en vlam?
BitFire! Op moment van schrijven zijn ze vrij nieuw, maar ze geven zelf aan al 20 jaar actief te zijn in het beveiligen van grote aantallen websites. Het aantal plugin downloads van BitFire op WordPress.org is op moment van schrijven nog rond de 100.
Ik ben natuurlijk enorm benieuwd wat deze “nieuwe speler” in de WordPress wereld te bieden heeft. Wat maakt hun anders dan WordFence, SolidWP, of 10 andere beveiligings plugins?
BitFire over hun dienst/plugin op WordPress.org
Klik op de afbeelding om de originele Engelse introductie op WordPress.org van hun plugin te lezen
[inn-1v3] [sluit-inn]
[sluit-inn]
[inn-2v3] [sluit-inn]
[sluit-inn]
[inn-3v3]En meer statements[sluit-inn]
Statements van BitFire vertaald in het Nederlands
- Ze claimen de enigste te zijn die tegen iedere 0-day lek beschermt sinds 2022.
Uilteg 0-day lekken: Dit zijn lekken die al in plugins of thema’s zitten het begin van de life-gang en zijn razend populair op internet, aangezien ze op vrijwel iedere release van een plugin of thema zouden kunnen werken. - Bot herkenning
Ze geven aan de werking/code te kennen van 3000 verschillende bots. Zo kunnen ze bezoekers onderscheiden van hack-bots. - 0-day exloit bescherming middels de Firewall uitvoerig getest
De bescherming tegen 0-day exploits blijken niet alleen in theorie te werken maar zich bewezen te hebben. - Geen onnodige vertraging van de website
Ze claimen 20x sneller te zijn dan WordFence, en geen onnodige vertraging te veroorzaken met de beveiligingsregels. - En nog meer statements..
Oké fijn de plugin is dus geweldig naar eigen zeggen
Ik weet hoe het gaat, je moet mensen laten weten wat je plugin allemaal kan. Maar in dit vakgebied is het erg lastig om iemand te overtuigen met statements hoe goed en snel een plugin is.
Hoe ga je dan merken of een plugin goed is?
Dat zal de tijd moeten bewijzen.
+ Wat wij nu maar gaan doen, is de plugin installeren en kijken hoe die eruit ziet, wat deze gratis versie kan, of er vastlopers zijn, false flags, hoe de malware scanner het doet etc etc.
BitFire installeren op WordPress
[inn-1v3e] [sluit-inn]
[sluit-inn]
[inn-2v3e]We installeren en activeren de BitFire plugin, en wat mij opvalt is dat er dan (nog) niets gebeurt. Nu hoor ik je denken: dat hoeft niet want beveiliging moet niet storen en gewoon op de achtergrond werken.
Maar héla! Ik wil wel weten dat de beveiliging “aan” staat. En een basisconfiguratie of minimaal introductie is wel zoals ik het gewend ben bij de andere grote spelers op het gebied van WordPress beveiliging.[sluit-inn]
Firewall configuratie
Oh, daar is tie. De configuratie, die ga je zien wanneer je de instellingen en andere menu items voor het eerst opent. Het betreft 5 stappen waarmee je de zuurtegraad van de firewall instelt.
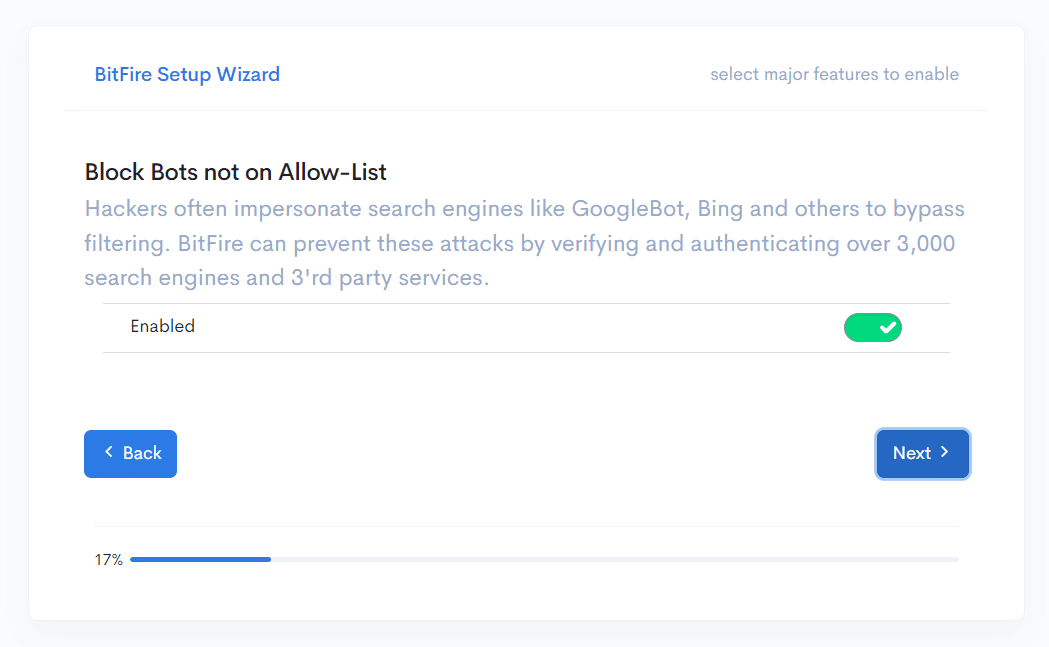
Nou mooi, er worden wat motivaties aangedragen om 5 functies aan te zetten. Waarbij weinig mensen bezwaar zullen tonen (als je het al gaat lezen).
Geen overdosis aan pagina’s en instellingen
[inn-2v3e]Misschien wel fijn dat er geen overdosis aan pagina’s met mogelijkheden en instellingen zijn? – In vergelijking met diverse andere beveiligings-plugins..
De 5 menu items die je kunt openen vereisen een cursus voordat je er iets mee kunt.
Er staat veel informatie, dat absoluut voor de doorgewinterde beveiliger bedoeld is en niet voor een beginner of voor de standaard WordPress website eigenaar.
[sluit-inn][inn-1v3e] [sluit-inn]
[sluit-inn]
Voor wie ze de plugin nu gebouwd hebben?? Die 3% aan fanatieke beveiligers?
De Malware scanner
Geen idee waarom.. maar van de malware scanner wordt ik altijd blij.
Geeft een vertrouwd gevoel, net als alle antivirus scanners in Windows en dergelijken.
Je drukt op een knop en de plugin gaat voor je zoeken naar Malware.
Let er even op dat je de standaard scan aan vinkt, anders neemt de Malware scanner niet alles mee.
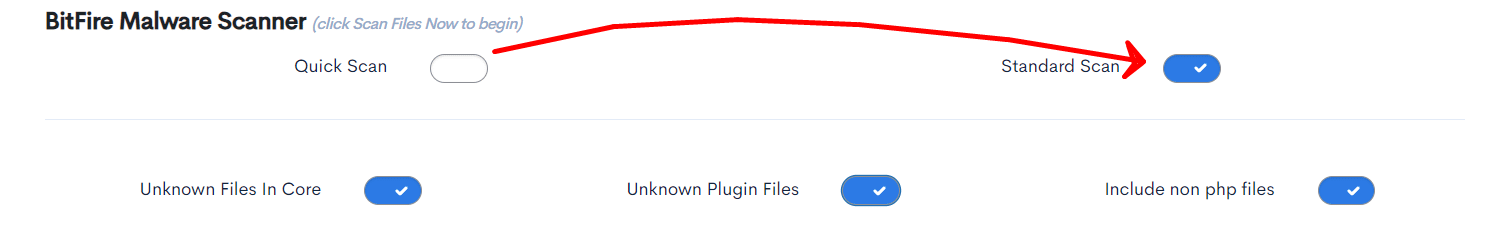
Het resultaat van de scanner is niet erg magisch, hij scant 5 tot 100 seconden, er draait een icoontje en er komt een balkje met de melding dat de integriteit van de website-bestanden goed is.
Het resultaat is niet geheel onverwachts aangezien dit een testdomein is met een verse WordPress installatie.
Wat wel opvalt is dat de melding dat alles oké is nogal onopvallend is. Het wordt groen, en wanneer je de pagina ververst is het weer blauw met een ander tekstje. De scanresultaten slaat hij zo te zien niet op.
![]()
![]()
Eindoordeel van de gratis BitFire plugin
BitFire is duidelijk ontwikkeld door ervaren programmeurs, door een team dat weet waar ze mee bezig zijn. Dat zie je in de informatie, in de specs die ze opgeven en de problemen bij andere beveiligingsplugins die ze zeggen te tackelen.
Er zit veel achter, maar het komt wat mij betreft nog niet zo naar voren.
Er zou mogelijk met meer introductie en begeleiding meer overtuigingskracht van de plugin uitgaan.
Zou ik BitFire gebruiken?
Nee, op dit moment niet. Ze moeten zich nog bewijzen, ze hebben op dit moment 4 reviews op deze gratis plugin met 100 downloads. Er zijn al genoeg andere doorgewinterde concurrenten. Denk aan SolidWP & WordFence & Sucuri.