What is a DDOS attack?
Understanding DDoS Attacks and How Hosting Providers Handle Them
DDoS stands for Distributed Denial of Service, which means that multiple computers continuously send requests to a server until its processing power or bandwidth reaches its maximum limit. Once the server reaches its limit, other requests (visits to websites) become impossible. Despite being fast, a server will continue to process requests until it can no longer handle them.
Can a Good Hosting Provider Be Temporarily Disabled?
Yes, any hosting provider can be affected, and even good hosting providers are susceptible to DDoS attacks because they often host important websites, making them prime targets. With enough people or infected computers, even a fast server with robust security can be overwhelmed, causing it to slow down or become temporarily disabled. This applies to large companies, informational websites, or web services alike.
Why Would Someone Launch a DDoS Attack on Your Hosting Provider?
DDoS attacks are sometimes launched by hackers to disrupt (often large) companies. The motivations behind such attacks can be due to political reasons, personal dislike for a company, or for possible financial gain. DDoS attacks are becoming more common because attackers can launch them easily from the comfort of their computers or network spaces, assuming they can remain anonymous.
DDoS attacks differ from DOS attacks, which are carried out by a single computer. DDoS attacks involve multiple computers or servers under the control of the attacker through a Botnet, which is a network of infected machines (e.g., Trojans, Worms).
What Can Hosting Providers Do About DDoS Attacks?
Hosting providers have several options, each with its pros and cons:
- Limiting the server’s speed in sections to ensure only a small number of websites go down at a time. However, this approach can still lead to an overload if a group of websites on the server receives a high number of requests, causing issues even with smaller attacks.
- Tightening security measures to reduce the number of requests and limit certain server functions. This approach affects all website owners as it restricts the functionality of their websites.
- Employing sufficient staff to monitor the server 24/7 and respond promptly to excessive requests. Some hosting providers adopt this strategy, but it is labor-intensive and costly, which may result in increased prices.
Does a Hosting Provider Have Poor Quality if Uptime Is Not 100%?
Not necessarily, occasional downtime can happen, but it becomes an issue if it occurs frequently or for prolonged periods. A good hosting provider should ensure that the server is quickly restored. This requires well-trained personnel who conduct preventive checks and act promptly when necessary.
Research and experience with various hosting providers have shown that many of them have uptimes ranging from 90% to 99%, which is high considering the constant global activity of internet criminals.
What Can You Do Against a DDoS Attack?
You can take several measures to protect your website from DDoS attacks:
1. Keep your website up-to-date to reduce the likelihood of hackers gaining access to the server.
2. Regularly create backups of your WordPress website. Store them securely at home or use an external backup service provided by your hosting provider.
By taking these precautions, you can minimize the impact of DDoS attacks and ensure the security of your website.

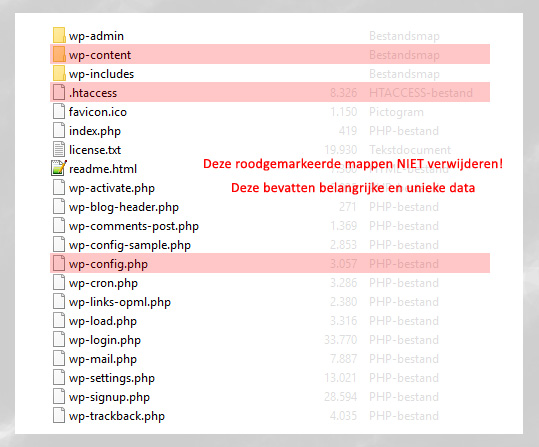
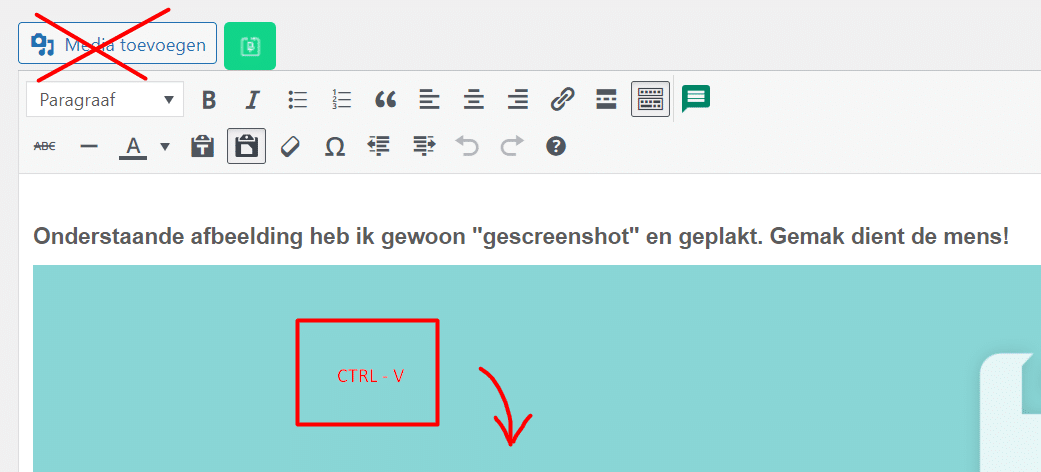

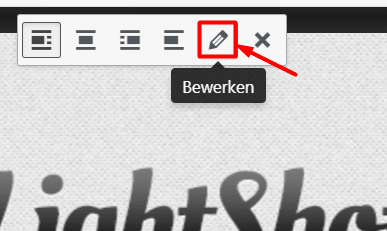 Je zou alts kunnen toevoegen, klik in je editor op de afbeelding en selecteer dan het potlood icoontje. En de bestandsnaam? Als je Google echt 101% te vriend wilt houden moet je de afbeeldingen toch los opslaan, een goede naam geven en dan uploaden.
Je zou alts kunnen toevoegen, klik in je editor op de afbeelding en selecteer dan het potlood icoontje. En de bestandsnaam? Als je Google echt 101% te vriend wilt houden moet je de afbeeldingen toch los opslaan, een goede naam geven en dan uploaden.