Hackers are very creative in creating scripts that are not recognized by the server, WordPress, or security plugins like WordFence & Ithemes security.
A hacker writes such scripts to use your website to advertise his own website where he displays sponsored ads or sells products.
There are several ways hackers can use your website to achieve this. As you read this article, you’ll understand why using a security plugin to scan your website is not enough to get rid of a hack.
WordPress hack 1: the cookie method
Using a cookie, the hack script is only loaded once per user. Due to this one-time activation, website owners may assume the hack is gone, if they even noticed it in the first place. The script is also programmed to be active only when a specific user agent is indicated. As a result, the server will not encounter the active script if the user agent is not detected as Chrome or mobile.
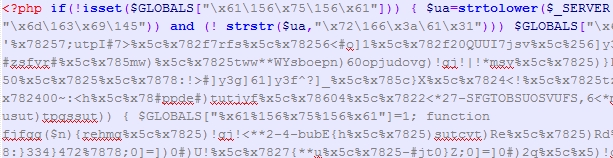
WordPress hack 2: the base64/eval method
The code is written in encoded PHP language, making it difficult for various scanners to detect which functions are being executed in a PHP file. The code is made up of numbers and letters, making it challenging to trace the source using a regular search & replace.
WordPress hack 3: the admin method
As a website owner, if you are logged in to the admin panel of WordPress, the hack is designed to disable itself when an administrator is logged in. This makes security scanners less effective or even completely ineffective.
WordPress hack 4: the iframe method
By using a simple line of code, a dynamic iframe can be loaded, allowing later pages to be called up with it. Since this is done via JavaScript, the code does not appear in the visible output of the source code.
To make matters worse, it is often designed to consider the host user, so not every browser will display the iframe.
By using inline code, the iframe is hidden from view.
WordPress hack 5: The Htaccess method
You could easily overlook this. In your root, you have the Htaccess file, which can redirect the browser to other pages. The trick that is often used is redirecting only Android devices to a domain where a file runs that redirects to another website from a list of malware sites at each visit. On a PC, you won’t see it, and you won’t be redirected.
In addition to these 5 methods we just discussed, there are many more possibilities that servers allow to redirect visitors to malicious websites. These methods are unknown to the regular programmer, and that’s why getting rid of a hack is not so straightforward.
As a WordPress website security specialist, I have seen a great number of tricks, and when the regular cleanup techniques such as thorough searching, updating, removing, and scanning do not yield results, it’s time to check the high-tech tricks.
To save yourself some sleepless nights and days of research, you can always contact WPbeveiligen.
With standard warranty and the possibility to extend WPbeveiligen’s service to a guarantee of 3, 6, or 12 months, you can be sure to have a secure website without having to have all the knowledge to preventively and actively block hackers and virus scripts.