
Indeed, hackers often encode their PHP scripts to make it harder for the server to quickly recognize them as viruses. The server won’t decode each file multiple times to read it.
However, such a file can still be executed upon request, and that’s what a hack script does.
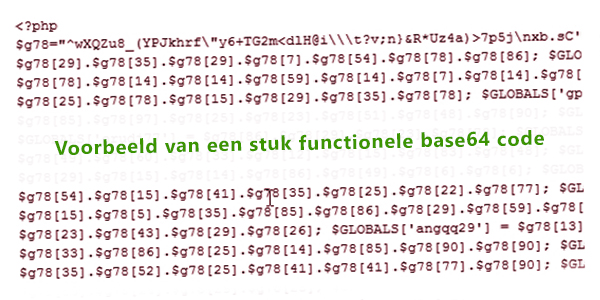
Decoding a piece of base64 code
When you see that whole mess of code, you may not know where to start. But there is some logic to it. The code often starts with an `eval(“”)` statement, where it wants to execute the code within the “”. You can put that code into a decoder.
They often put the code in a variable that must be executed via a decoded variable, making it difficult for someone to unravel it. And that’s precisely the intention of the scriptwriters.
What is usually hidden behind “that hidden code”?
In many cases, it’s a link to a product page of the hacker or their client. Or a script that sends emails (spam) to email addresses.
But sometimes you’re dealing with a more advanced hack script that not only performs those simple actions but also transfers your database information or creates a new user in the database so that the hack script can regain access later, even if you have repaired it.
Or a script copies itself to every directory on your server.
These are things you probably don’t want to know, and it’s best not to put yourself in the shoes of a scriptwriter but rather remove it and partially renew your WordPress to ensure that all of its code and files are gone from your server.
The base64 code is encoded 3-10 times.. what now?
The files are often encoded 1-5 times. This means you could spend quite some time decoding them.
Fortunately, there is a website that can do this process for you. UnPHP creates a virtual space and extracts the encoded PHP from it.
It can handle up to 81 iterations in a loop if needed!!




