The chance is high that during your search for a hack or malware on your website, you didn’t even think about the uploads folders.
But did you know that this is one of the most commonly used places for hacks?
The uploads folders are writable
The uploads folders are writable, and it’s a good hiding place.
Both plugins, the theme, and WordPress itself have permissions to place files there.
Finding a hack in the uploads folder from 2015
How quickly can you find a hack that is in the folder 2015 / 07?! You wouldn’t expect it, but that’s where the uploads from 2015 are, right?!
Resetting the upload date
The trick they use is resetting the upload date.
Scripts can manipulate that date to make you think they have been there for years.
That means they upload the hack, the backdoor this week or month, but manipulate the file’s write date so that you won’t discover it easily.
They make it look like the file has been there for years!
Okay, all these tricks from hackers and their scripts are worthless, but with this knowledge in mind, the question remains:
How can I find a hack, malware, or backdoor in the uploads folders?
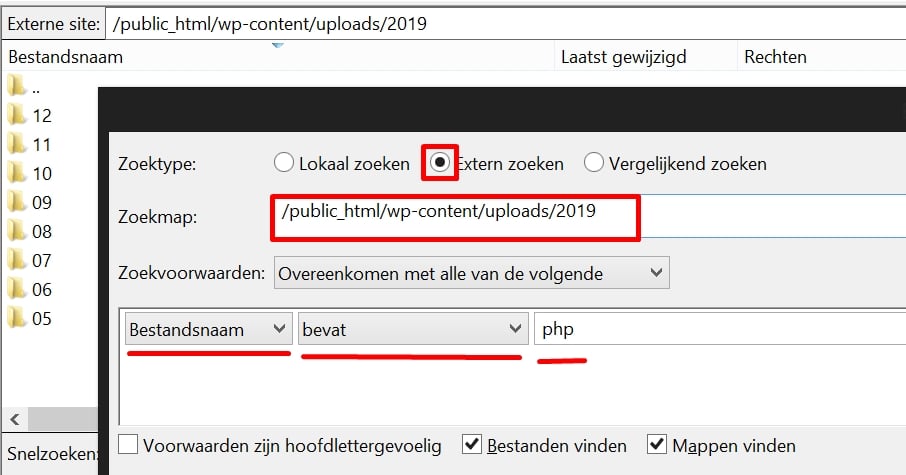
Search for PHP files
A hack file usually serves a purpose, and it can only do that if it’s a PHP file.
So, you take an FTP program like FileZilla and press F3, which opens the search window. Then you search in the uploads folders for a file with the name or extension PHP.
Is a PHP file all you should look for?
No, unfortunately, hackers also know that you and scanners search for PHP files. Additionally, security plugins are aware of that trick and restrict PHP execution in the uploads folders.
So, what hackers do is upload a file with the name server-att.php.jpeg (for example).
What does the scanner think? It thinks it’s a JPEG file because that’s the last part of the extension.
Meanwhile, another script still loads this file as PHP and executes the hack.
ICO files, JPEGs with a PHP extension in the name, also require attention.
External scanning
It may be necessary to scan the files for Trojans, malware, and backdoors.
As you just read, advanced hacks are hidden.
Download your uploads folders to your PC/Mac and run them through your antivirus scanner.
You can also upload the files to virustotal.com.
This website checks the files against a large database of antivirus software, increasing the chances of detecting a hack file.
Note: The virustotal website does not accept gigabytes of information, so you’ll need to compress and/or split the files to scan them.
Found a hack in the uploads folder, what now?
Once you’ve discovered it, simply delete it. Then check if the rest of your website is not infected because such a hack file usually serves a purpose and doesn’t stand alone.
But
I don’t have time, it’s complicated
If you’re too busy or find it too complicated, I understand. It’s a specialized field.
You can also leave this work to us.
We remove hacks, secure WordPress websites, and ensure that YOU have no worries.
Take advantage of our service or contact us for any questions!